The Cobalt Strike team is excited to sponsor the Darknet Diaries podcast, which brings awareness to critical cybersecurity issues and encourages proactive efforts that bolster defenses against modern threats and attackers.
Cobalt Strike is a threat emulation tool that enables security professionals to simulate the tactics and techniques of a stealthy long-term embedded attacker in an IT environment.
Cobalt Strike: A Benchmark Solution
Cobalt Strike supports red team engagements by prioritizing operator flexibility with a malleable C2 framework and Beacon, an adaptable signature payload.
Users can tailor engagements to suit their needs and can easily incorporate their own tools and techniques, as well as the tools of the Cobalt Strike user community.
Cobalt Strike has always prioritized operator flexibility, with new features like:
BeaconGate
Cobalt Strike’s latest release introduces BeaconGate, which further enhances operator flexibility by enabling customization of how API calls are handled. Users can now implement bleeding edge call stack spoofing TTPs and apply them universally to Beacon’s WinAPI calls.
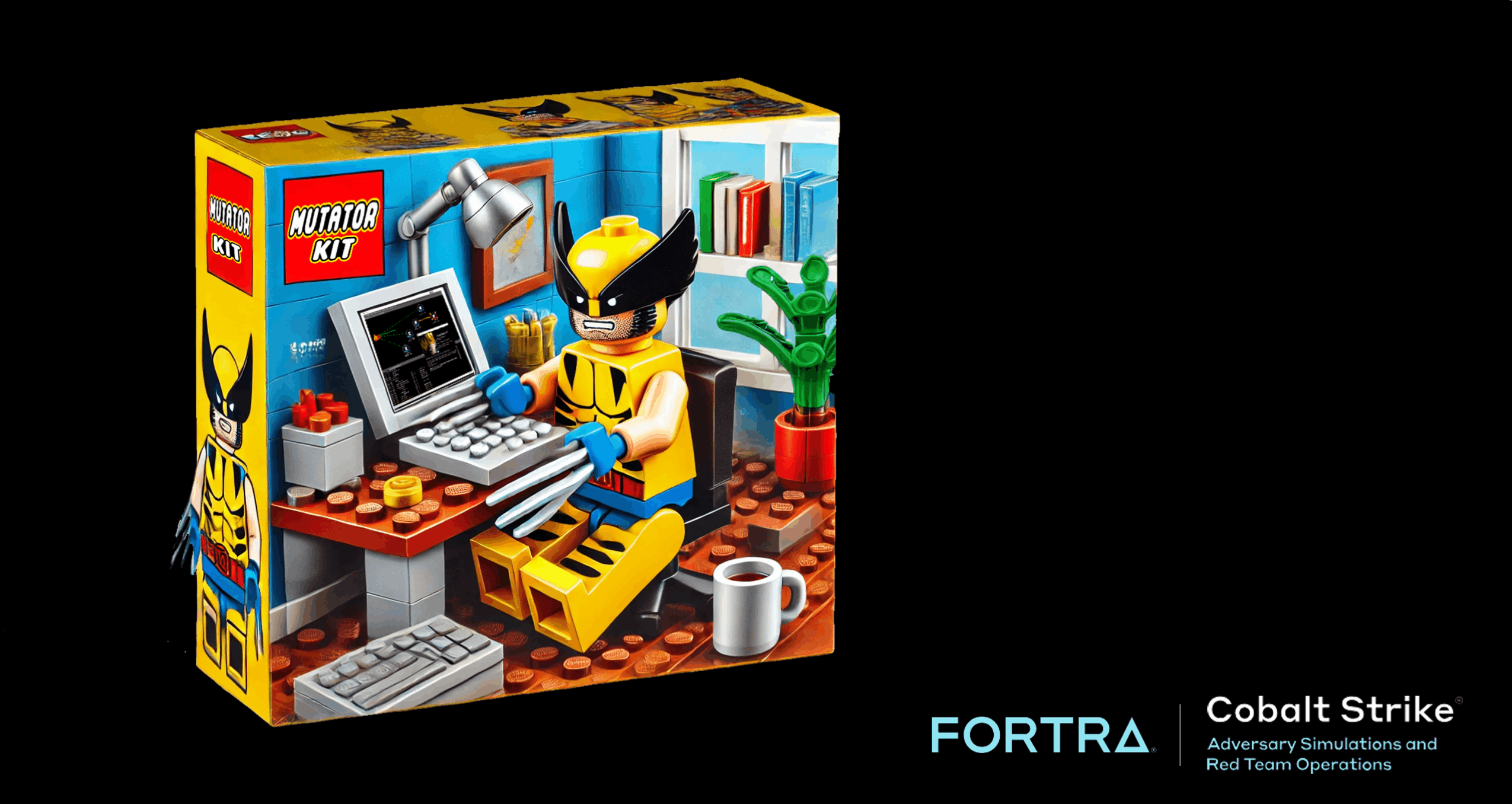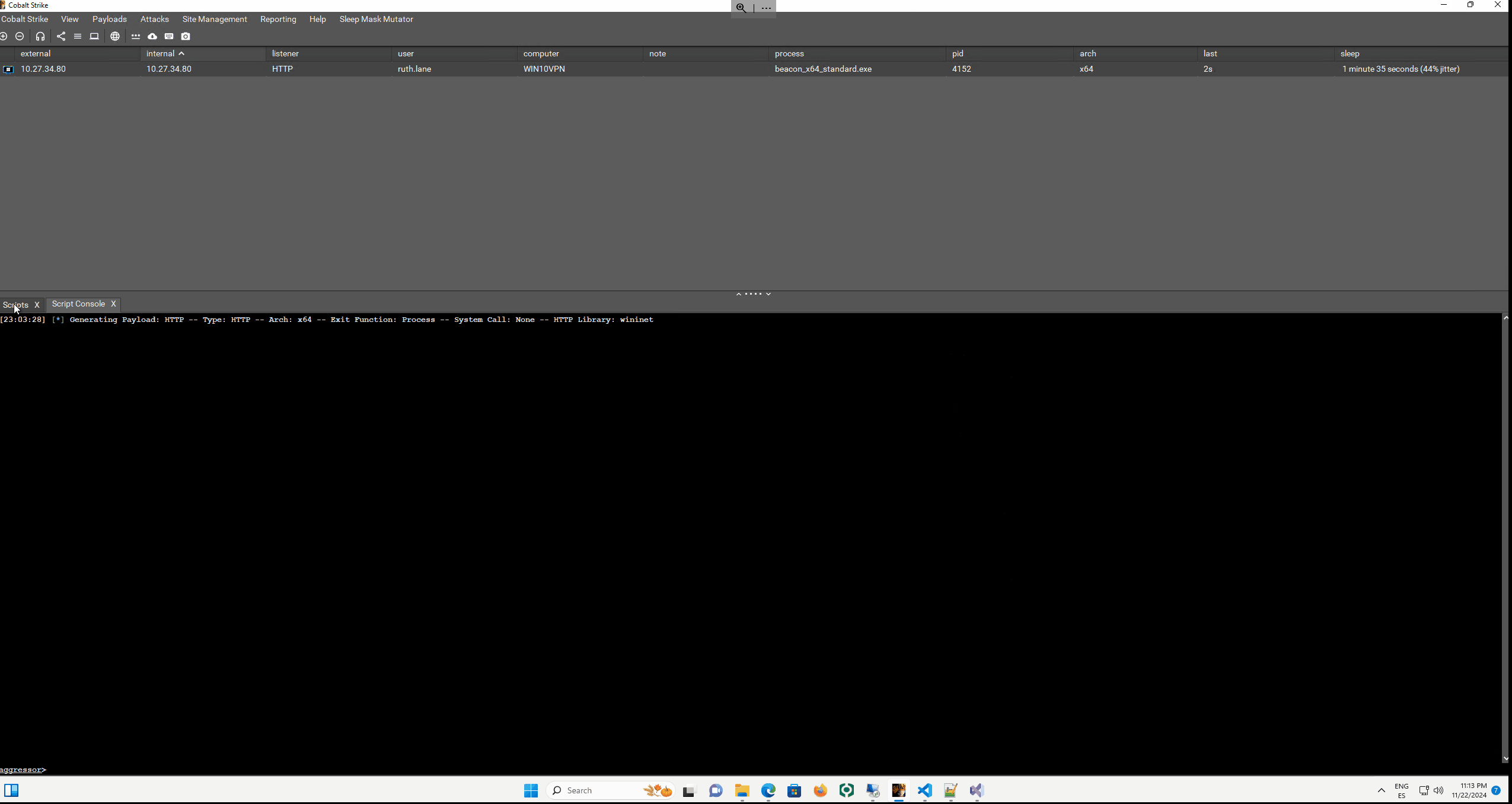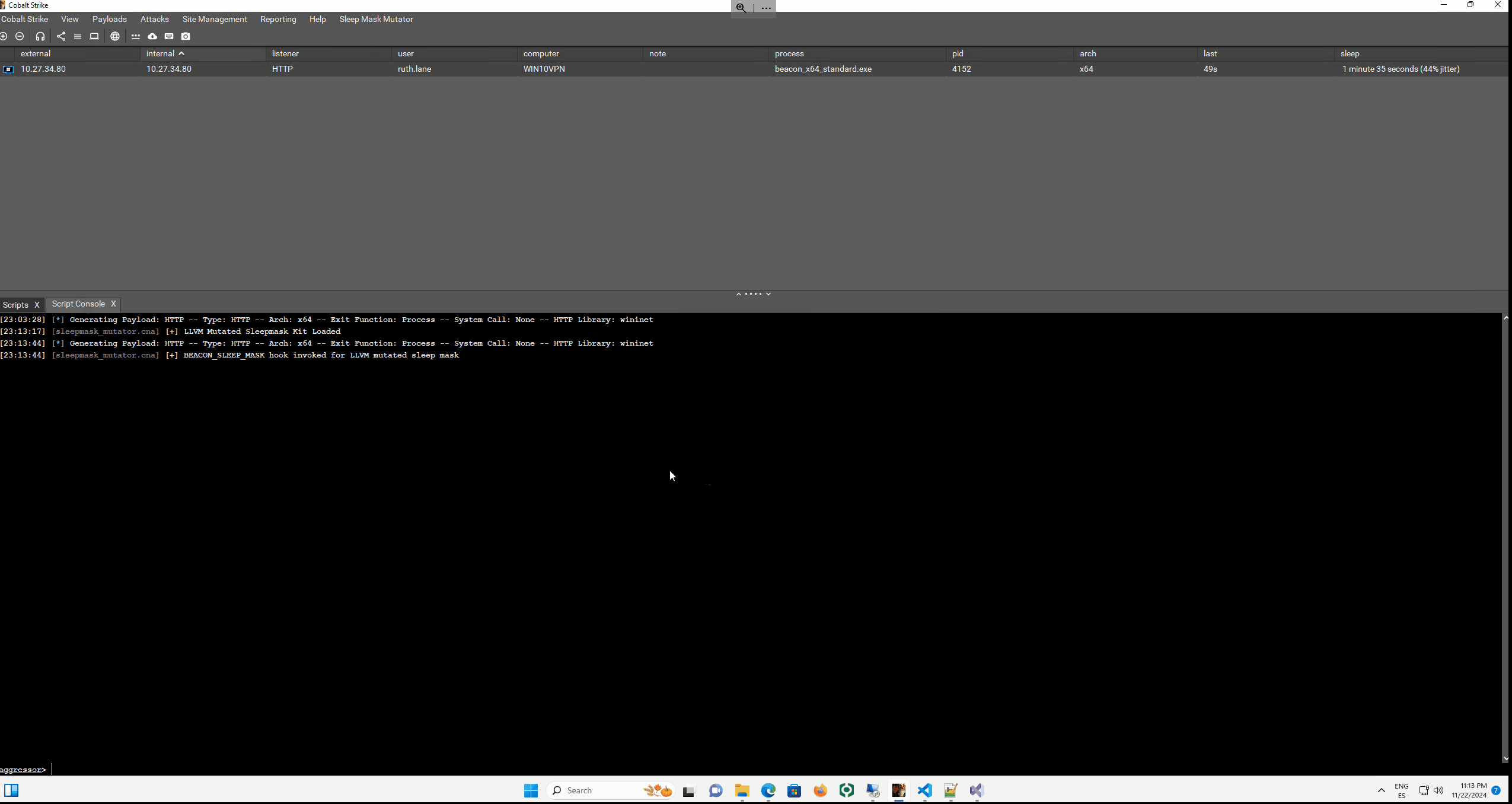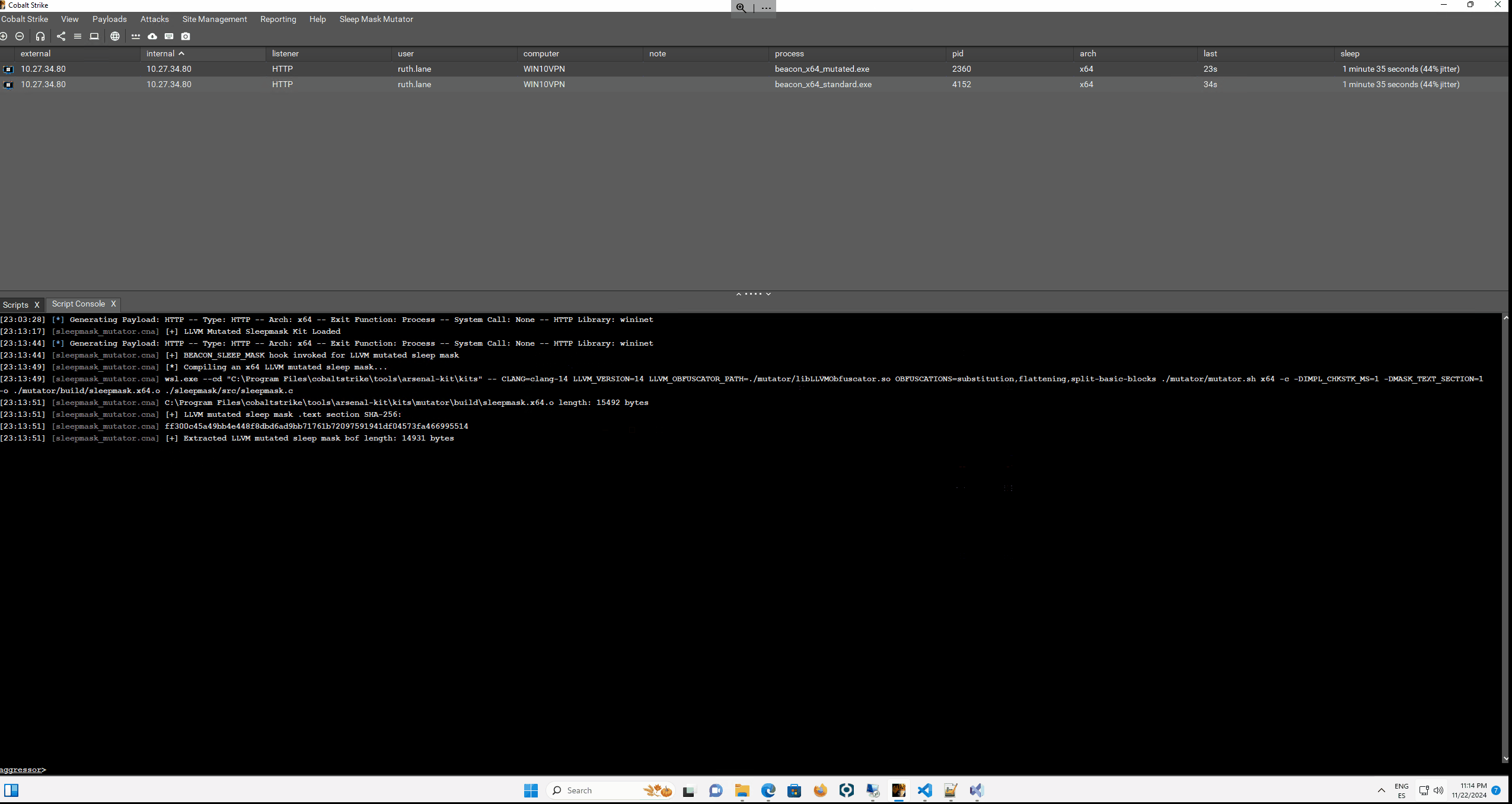
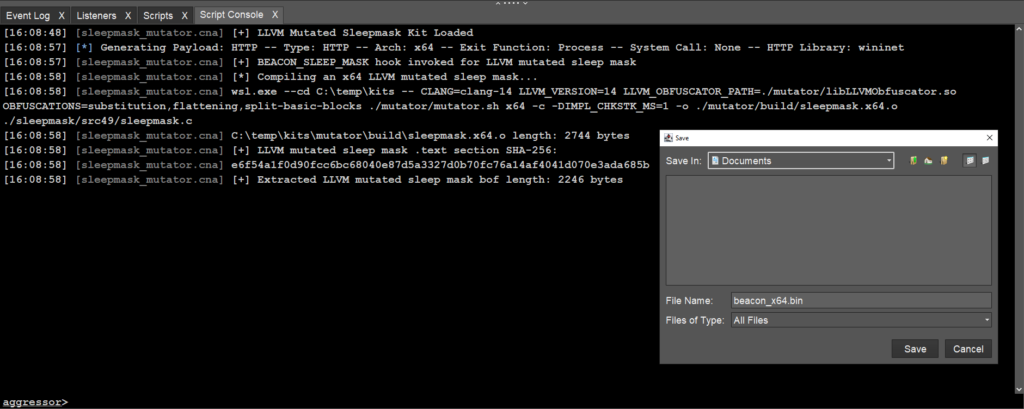
Mutator Kit
Another recent addition is the Mutator Kit, which can prevent detection by YARA signatures and memory scanning tools. It can create unique variations of the sleep mask functionality using LLVM (Low Level Virtual Machine) obfuscation techniques to modify code patterns.
UDRLS
User-Defined Reflective Loaders (UDRLS) have also been newly expanded. UDRLS are a way for users to write and bring their own tradecraft to bear. UDRLs are particularly helpful for increasing the evasiveness of Beacon by allowing operators to use a loader that works for their particular engagement.
Ungated Resources to Explore
Stay up to date on releases, takedown efforts, research initiatives, & more
Further Amplify Engagements with the Red Team Suite
Outflank Security Tooling (OST) is an evasive toolkit made for red teamers by red teamers. It is built for performing in mature and sensitive target environments to efficiently simulate techniques currently used by APTs and other cyber attackers. OST’s toolkit has coverage for every aspect of an engagement, with tools for initial breach, lateral movements, privilege escalation, achieving persistence, and final exfiltration.
Get an overview of OST in this short demo:
Cobalt Strike and OST can be packaged together at a discounted rate, enabling organizations to benefit from red teaming tools that seamlessly integrate with one another. For teams seeking enhanced capabilities, the Red Team Suite adds exclusive access to additional cutting edge tooling from Cobalt Strike Research Labs, which is unavailable when purchasing products separately.
Bundle Cobalt Strike
Get additional offensive security tooling coverage and access special pricing when combining Cobalt Strike and Outflank Security Tooling.

