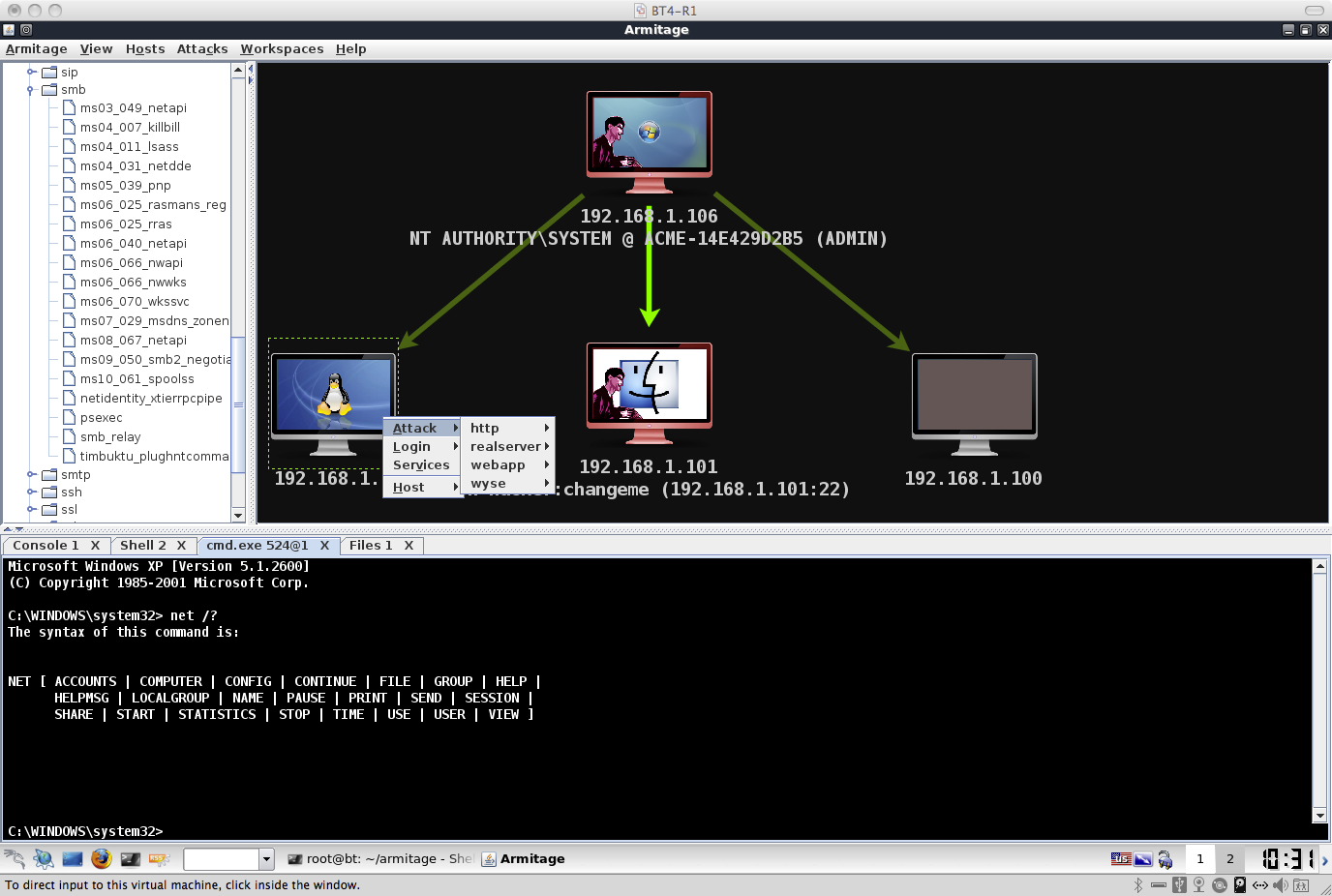
Today marks the two-year anniversary of the release of Armitage. My goal was to create a collaboration tool for exercise red teams. I wanted to show up to North East CCDC with a new toy. I had no idea Armitage would lead to so many new friends and new adventures.
In the past two years, Armitage has had 55 releases and over 900 commits to the repository on Google Code. Today, Armitage is 11,721 lines of Java code and 10,155 lines of Sleep code.
Armitage has appeared on a Fox sitcom (thanks Erik!), in many articles, on the cover of two magazines, in the pages of multiple books, in classrooms all over the world, and it has had its share of press. Armitage’s scripting technology Cortana, was funded by DARPA’s Cyber Fast Track program.
Early Armitage with the 3-Panel Interface
Armitage is quite the ride. I have not seen this type of response to my other projects. As Armitage hits maturity, I ask: how do I innovate without creating bloat or damaging Armitage’s core use case?
My answer is to keep Armitage focused on its core capability: sharing the Metasploit Framework. Cortana is a natural progression of this work. It allows you to share the Metasploit Framework with bots. Next? I’m keen to link multiple instances of the Metasploit Framework and share them in an intuitive way.
Armitage’s Oldest Screenshot
My North East CCDC red team experiences led to Armitage. In the CCDC red team environment, the lack of collaboration was a big pain. Armitage was my crack at this problem.
Armitage’s big brother, Cobalt Strike, has a similar story. I used to provide red team services to a DoD customer. From this work, I have a wish list of capabilities and an appreciation for the process that ties them together.
Cobalt Strike is a system to penetrate networks the way real attackers do. I use Armitage and the Metasploit Framework as an integration point for the tools on my wish list.
I’m working through this wish list, one capability at a time. Here’s what I’ve got, so far: To get a foothold, Cobalt Strike offers a workflow for web drive-by and spear phishing attacks. To quietly hold access, you get Beacon, a post-exploitation agent that uses DNS to check for tasks. To use your foothold, Covert VPN bridges you into the target’s network. Of course, Cobalt Strike generates MS Word and PDF reports too.
This work is fun. Armitage is a vehicle to experiment with collaboration, automation, and scale. Cobalt Strike is my way to help penetration testing become threat emulation again.
I really had no idea that two years would lead to this. What a crazy ride!