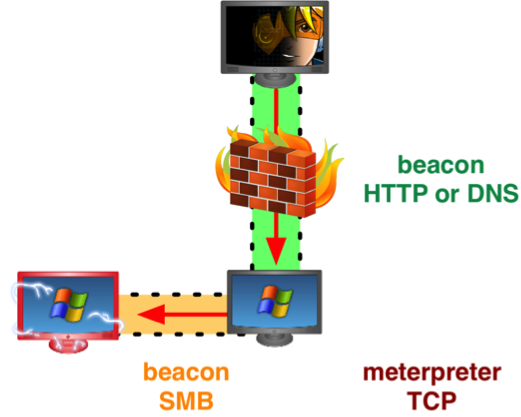
I write so many blog posts about Beacon, I should just give up and call this the Beacon blog. Beacon is Cobalt Strike’s post-exploitation agent that focuses on communication flexibility and added covert channels.
It’s also possible to tunnel Meterpreter through Beacon with the meterpreter command. In this blog post, I’ll explain how this feature works.
Beacon exposes a SOCKS proxy server to allow the Metasploit Framework and third-party tools to pivot through a Beacon. Each time Beacon checks in, data to write to and data read from ongoing connections is exchanged.
When you type ‘meterpreter’ in a Beacon, two things happen. First I generate a task to make the Beacon check-in multiple times each second. I call this interactive mode. Next, I issue a task that injects a bind_tcp stager into memory on the target. This stager binds to a random high port on 127.0.0.1. A lot of host-based firewalls ignore activity to services bound to localhost.
Once the above steps are complete, Cobalt Strike’s C2 server gets a response from the Beacon stating it’s ready to stage the Meterpreter payload. I stand up a one-time-use SOCKS-compatible port forward. This port forward ignores the client’s specification about which host to connect to. It always connects to 127.0.0.1. I do this because I want the Metasploit Framework to associate the Meterpreter session with the hosts IP, but I want it to stage to localhost.
I then start exploit/multi/handler for windows/meterpreter/bind_tcp. I configure this module to use my SOCKS-compatible port forward with the Proxies option. The Proxies option in the Metasploit Framework allows me to force an outbound Metasploit module through an arbitrary SOCKS proxy. I set RHOST to the IP address of my target.
The handler for Meterpreter bounces through my port forward to hit the bind_tcp stager I put into memory earlier. The payload stages over this connection and then the stager passes control to the Meterpreter payload with the same socket in the EDI register [a detail managed by the stager and the stage].
At this point, I have a Meterpreter session that tunnels through Beacon. Better, I have this session without interference from a host-based firewall (if there is one).