TL;DR Beacon is a new Cobalt Strike payload that uses DNS to reduce the need to talk directly to Cobalt Strike. Beacon helps you mimic the low and slow command and control popular with APT and malware.
In the interest of helping you verify vulnerabilities for compliance purposes, I’d like to introduce you to Beacon, a new feature in the latest Cobalt Strike update.
Beacon is a PCI compliant payload (if PCI means Payload for Covert Interaction). Beacon offers long-term asynchronous command and control of a compromised host. It works like other Metasploit Framework payloads. You may embed it into an executable, add it to a document, or deliver it with a client-side exploit.
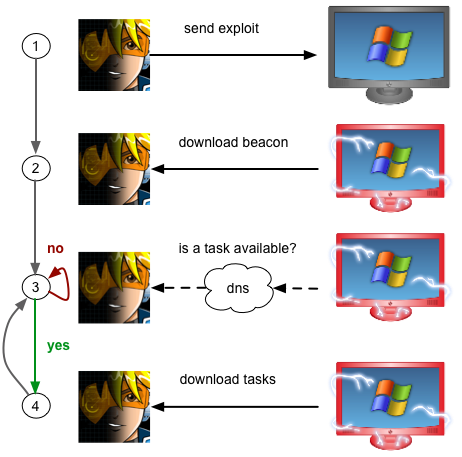
The next time you have to run an exploit to check the box, why don’t you exploit the CEO’s system and use Beacon to quietly maintain a lifeline into the network until everyone is gone for the night? Then you can inject Meterpreter into memory, load Cobalt Strike’s Covert VPN, and run your favorite vulnerability scanner
What is that you say? Your customer has decent network monitoring? They’ll block your beacon before anything can be done about it? OK! Beacon can phone home to multiple domains. If one gets blocked, that’s OK. If you own a few domains and have a few NS records to spare, Beacon can check for tasks using DNS requests. It doesn’t need to communicate with you unless a task is waiting for it.
Beacon’s features include
- Check task availability using HTTP or DNS
- Beacon to multiple domains (who cares if that first one is blocked)
- Capable of automatic migration immediately after staging
- Tight integration with Cobalt Strike. Deliver beacon with social engineering packages, client-side exploits, and session passing
- Intuitive console to manage and task multiple beacons at once
Beacon is available in the latest Cobalt Strike trial.
Licensed users may use the update program to update their Cobalt Strike installation to the latest version.
If you’re at DerbyCon, make sure you stop by the Strategic Cyber LLC table for a demo.Are you headed to OWASP AppSec USA in Austin, TX? I’m teaching a two-day Advanced Threat Tactics course. In this course, I will show you how to evade defense technologies, gain a foothold in a modern network, and carry out post-exploitation. It’s a great way to learn more about how to use technologies like Beacon